System Management
- • How to add alias of domain?
- • What is COS?
- • Why can't I assign to user after creating a new COS?
- • How to set mail space and the size of attachment?
- • How to set mail only send/receive within internal site?
- • How to check the situation about mailbox space?
- • What file can you delete when the system capacity is full?
- • How to query log?
- • How to export mail and backup mail?
- • What log do you need to clear?
- • How to check logs for bounce letter?
- • How to check the inactive user within this month?
- • How to handle the situation that authorization server is error and the server can not work?
- • How to change welcome letter?
- • How to change LOGO in Webmail login interface?
- • How to set the time about timeout session?
- • How to access to API?
- • How to set the prohibitive type of attachment?
- • We bought monitor feature but can not find it in management page?
- • How to set the SPF record?
- • How to set the DMARC record?
- • About DMARC record
How to add alias about domain?
The administrator log in system. (Management interface - Enterprise Configeration - Domain Management), click domain to enter into editing domain page:
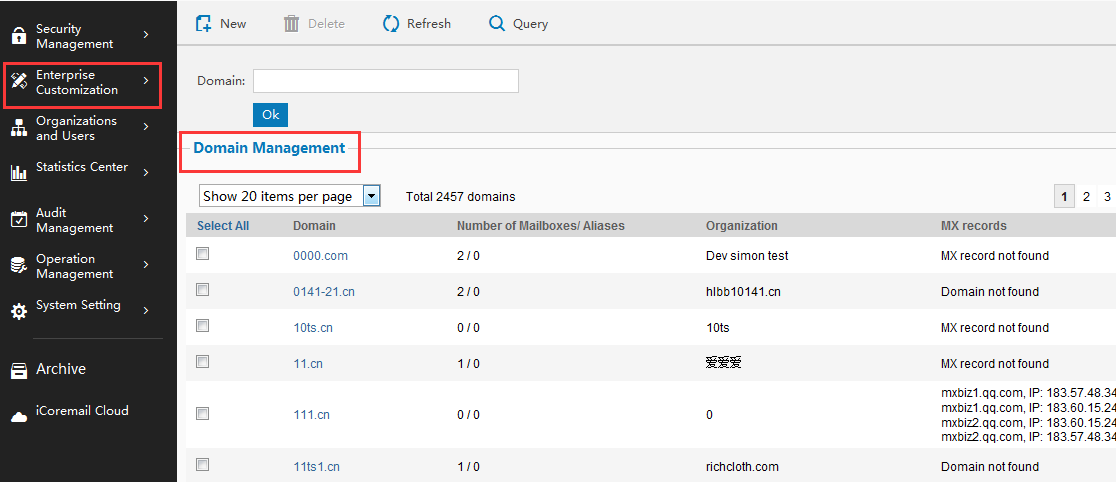
Enter domain alias and click "create" and add new domain alias.
What is COS?
Coremail divides mailbox service into different level according to use different customer requirement. And every level of COS is the set of certain service. Every mailbox is connected with the specified service (COS).
Why can't I assign to user after creating a new COS?
After adding a new COS, it need to be assigned to Org. Open the organization management page, you can add new COS in "Select COS" to "Add COS" to save it.
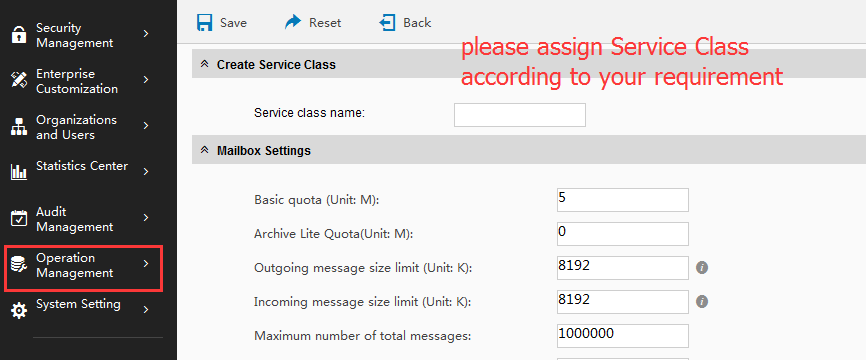
How to set mail space and the size of attachment?
Coremail system limit mailbox space and mail size by using COS. If the administrator would like to set this option, go to system administrator interface (Management interface - Operation Management-COS-Edit COS). If the size of receiving attachment needs to be limited, it can be changed in this option: Limit of size for mails(Unit:K).
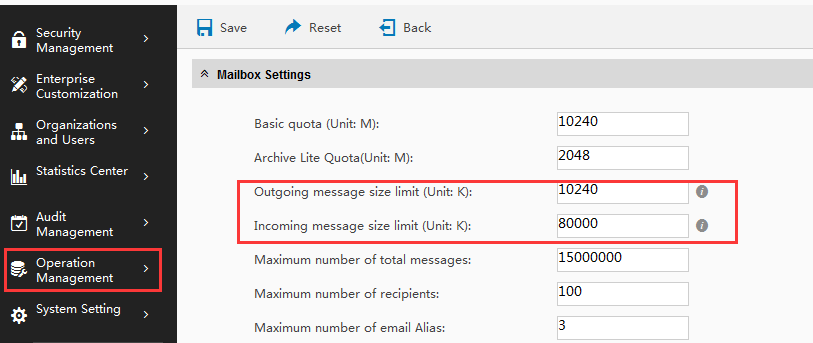
As the limit of receiving mail includes mail text and attachment. If users need to receive mega attachment, please expand the limit value. And the number coding make the actual size of mail bigger in exchanging, it is suggested that larger number will be better. For example the limit of user's mail (including attachment) is 10M, and the option value is 12M.
How to set mail only send/receive within internal site?
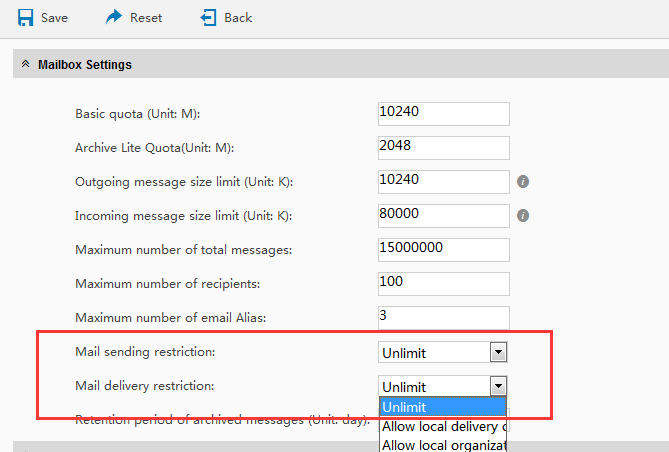
The administrator can change this option in system management interface - COS management, and click into "Edit-COS". In the field of "Mailbox limit", you can only allow internal send/receive by setting "Limit Mail Delivery" and "Limit Mail Sending". The mail binding with this COS only can be sent and received in local site.
How to check the situation about mailbox space?
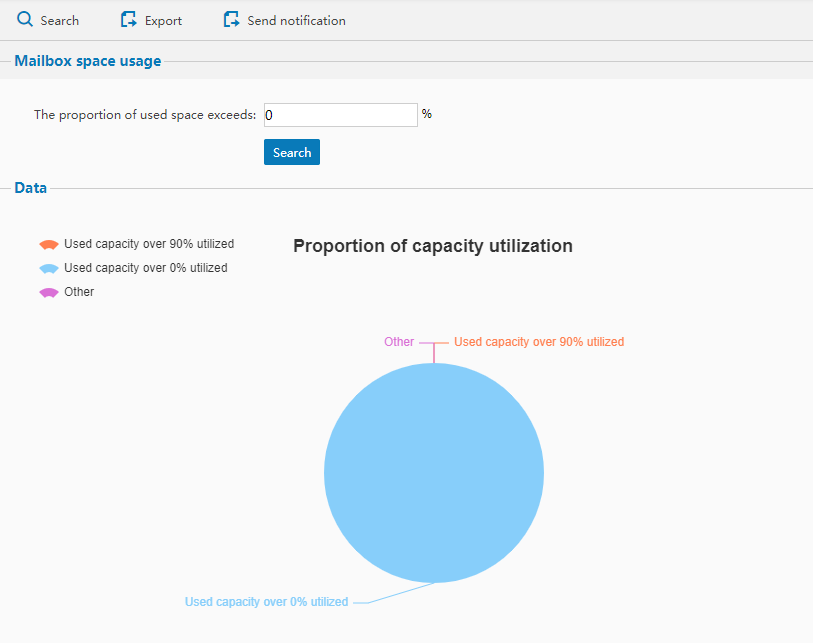
You can click system management interface - User Mailbox Usage Information and enter the proportion of space usage. The system will display the users that exceed the proportion.
What file can you delete when the system capacity is full?
Logs are stored in the path: directory/logs/backup. If the space of system is full, you can consider to transfer these files. (For example you can tranfer these files to server that specified for backup logs) And then delete these files.
How to query log?
You can view in system management interface - Audit management. Check administrator and user operation logs in this path.
You can view in system management interface- openration management - log view. And view Server Logs, Mail Delivery Log, Delivery Failure log and Netfolder Operation Log.
-
Click to enter into operation logs page to set your search time. And you can view the operators, the project in certain time and operation results.
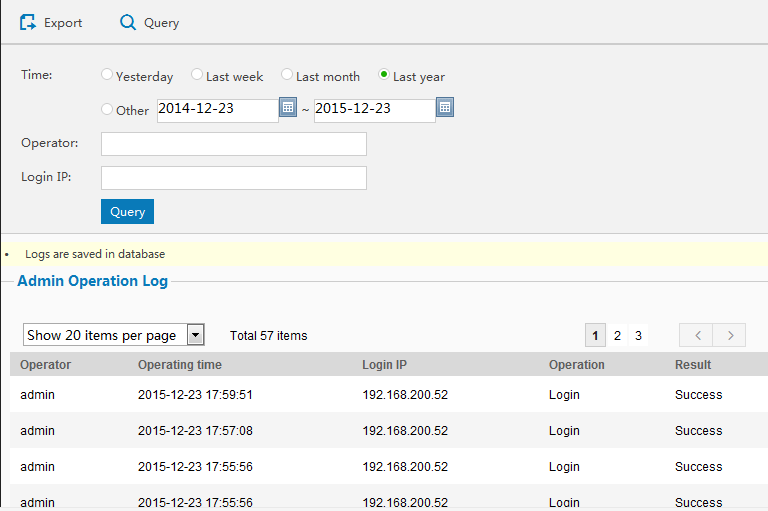
-
Click to enter into user operation logs page to set your search time.And you can view the operators,the project in certain time and operation results.
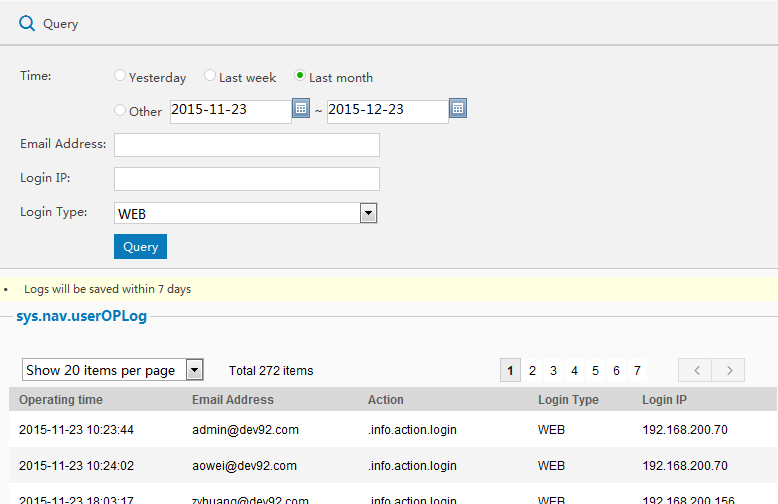
-
Click to enter into user operation logs page to set your search time. And you can view the operators, the project in certain time and operation results.
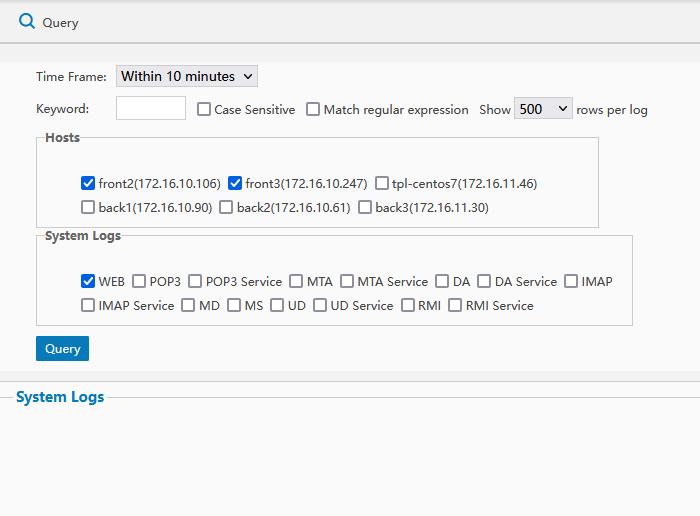 The description of service modules and its function:
The description of service modules and its function:
Modules Description MTA Server(Message Transport Agent) SMTP protocol is a protocol between Internet and Coremail mail system, including SMTP service, DeliverAgent (DA:sending agent) and two assiting module: scequerysvr (Network search management) and scecachesvr (Cache Management). Webmail Provide mail service based on accessing to pages. You can browse mail pages, sending and receiving mails. POP In charge of handling request of POP3 from client, and return corresponding message according to POP3 protocol. MD Server (mdsvr) Locate user information UD Server (udsvr) Storing and accessing to user data and mail index. MS Server (mssvr) Provide service of accessing and managing mail. Admin Server (adminsvr) In charge of system configuration and system maintenance and management
How to export mail and backup mail?
- If I know the ID of the mail, how to export the mail?
- Search the corresponding deliveragent.log to get the mail id.
- You can search the corresponding date in mssvr.log through mid to get the path of mail.
- You can use cat or more to view /data/11/111/111/tbms1s_asdfasfasdfasdf or use download tool to download this mail.
- Back up mysql database, you can pack and transfer under the directory /home/mysql/data in mysql database.
- Backup address, user information and save mail system information in mysql database. The iaddress of m_user_bin_data is to store address books and the address of cm_user_info is to store user address.
- Backup mail system, backup data: configuration files (conf,bin,lib,libexec,var in coremail directory, you can backup log directory logs if the space is enough.) Backup mail index/index directory, backup user mail/data directory, backup mysql database.
What log do you need to clear?
You can check these two logs: /home/coremail/logs/access_log & /home/coremail/logs/error_log. If these two files exceed 2G, the apache will fail to start.
How to check logs for bounce letter?
You can check mtasvr.log and deliveragent.log. If mail is rejected, you can find out problem in corresponding date directory of mtatrans.
How to check the inactive user within this month?
Run "$ mysql -ucoremail -p cmxt -e "select user_id ,org_id from cm_user_pref where lastdate<'2009-12-12 00:00:00';" > userlsp.txt" in the mysql machine.
How to handle the situation that authorization server is error and the server can not work?
It may be the limit of license and it causes ms failure. You can delete redundant user and please contact our commercial business if you need to add new users.
How to change welcome letter?
You can edit in system management interface. (Configuration and management - Page Customize - Edit welcome letter)
How to change LOGO in Webmail login interface?
If the administrator would like to change Webmail login interface into Company LOGO, he or she can replace files "logo.gif" and "title.gif" under Coremail\web\html\common\login.Note:the name of picture must be the same as before and the size.
The type of uploaded logo can be GIP, JPG or PNG. Recommended Size: less than 16,384 byte.
Notes:- The pixel of logo in Webmail is 212 x 70 and its format is gif.
- After logging in webmail, the pixel of logo in Webmail is 212 x 40 and its format is gif.
- The logo in log in interface save to /home/coremail/web/html/common/login. You can change gif format and upload to the folder, and then change the picture name as logo.gif.
- If you would like to change the picture of logging in webmail,please save it to /home/coremail/web/html/common/login. In directory, the uploading picture is gif. If the picture is other format, you need to open webapp/index.jsp,to find out "/common/login/logo.gif" and change logo.gif as the name of picture you need. The size is controlled in 480*55 and 50K to avoid logging page loading.
- Additionally, the LOGO in the upper left of management interface after loging in can not be changed, because it is in packing files.
How to set the time about timeout session?
You can set in the system management interface - Security Management - Login Settings :
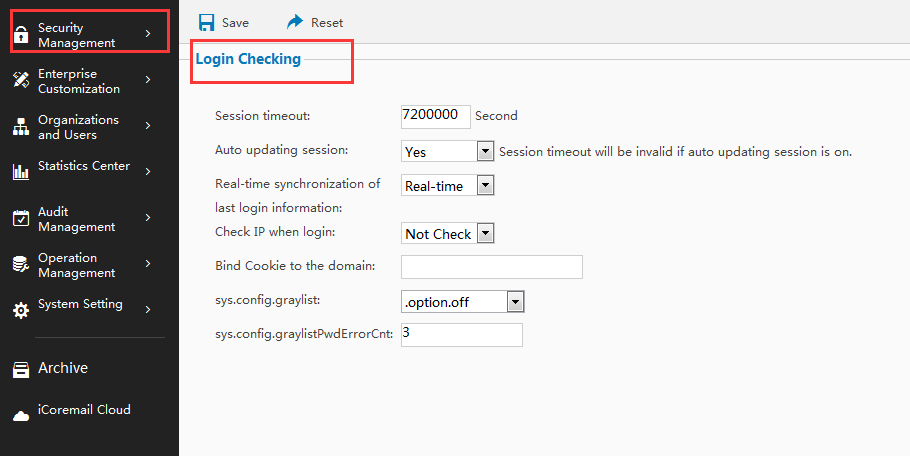
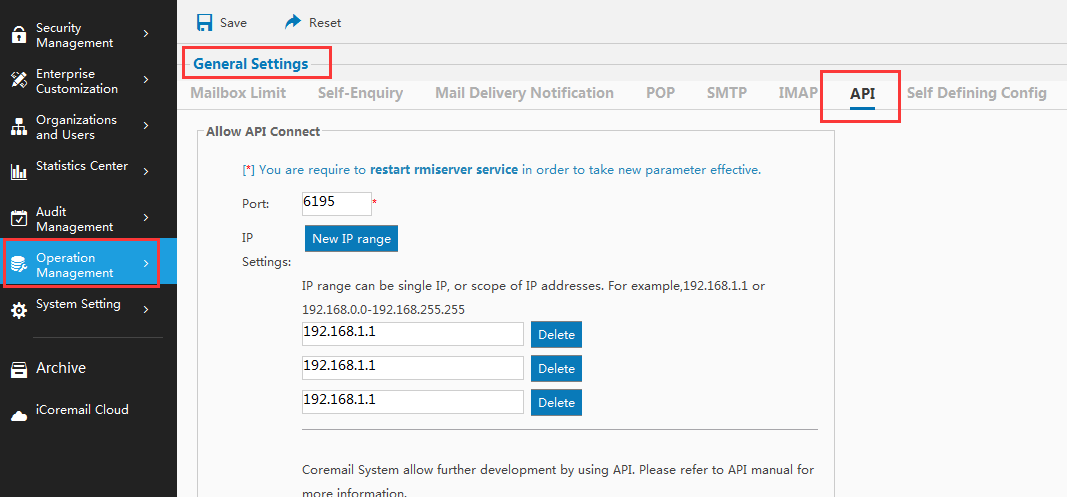
How to access to API?
Please select IP allowed to access before accessing to API, and you can add new IP in system management interface - system Settings - Common Settings - global settings - API.
How to set prohibitive type of attachment?
For the safety of mailbox, you can set some forbidden types of attachments in Configuration - Global settings - favorite settings - mail safety.
We bought monitor feature but can not find it in management page?
If you are super administrator, you need to monitor and audit mail in the way of organization administrator. Click into organization information page and "Manage the Organization" to enter into the management interface of this organization.
Please refer to mail monitor and audit guideline.
How to set the SPF record?
- What is SPF?
- How to set the SPF record in the domain mailbox?
Abbreviation of Sender Policy Framework. It is a technology to identify email sender by using IP address, it is a very efficient spam solution.
Recipient will first check the SPF record of the domain to determine whether the sender's IP address is included in the SPF record, if the address is in the record, that it is an correct message, otherwise it will be considered as a fake message and bounce back.
In order to improve the successful sending ratio of outbound mail, we suggest you set a TXT record of domain to avoid this situation.
TXT record is: v=spf1 include:spf.icoremail.net -all
How to set the DMARC record?
Dear business users:
DMARC has been designed based on real-world experience by some of the world’s largest email senders and receivers deploying SPF and DKIM. The specification takes into account the fact that it is nearly impossible for an organization to flip a switch to production. There are a number of built-in methods for “throttling” the DMARC processing so that all parties can ease into full deployment over time.
We strongly recommend that you set the DNS record to support by DMARC protocols, the following is a world surplus Mail DMARC setting method. If you have any questions in DMARC setting, please contact our service team: 400-888-2488, or email : 400kf@icoremail.cn.
Before setting DMARC records, your company must ensure that the record has been set as follows SPF:
v=spf1 include:spf.icoremail.net -all
After you set the SPF record, recommend your company to be set as follows DMARC record:
v=DMARC1; p=none; fo=1; ruf=mailto:dmarc@icoremail.cn; rua=mailto:dmarc_report@icoremail.cn
Parameter Description:
p:To inform the recipient, when a message is detected the presence of forgery I (sender) and the recipient to make any treatment, handling lighter to heavier followed: none is do without any treatment; quarantine is to mark messages as spam; reject is to reject the message. The initial proposal is set to none.
sp:DMARC recording sub domain take effect, a statement that has been forged in the sub-domain, the recipient must make the approach.
rua:After the detection of the recipient for the period of the summary report, which is sent to the e-mail address.
ruf:When detecting forged messages, the recipient must send the report the fake message to this e-mail address.
We recommend that you set using the DMARC records. In the initial period, p = set to none, a period of time by e-mail exchanges, can understand the situation in your domain being modeled from the recipient's feedback.
For rua and ruf two records, if you have a professional operation and maintenance, you can choose to receive and analyze the feedback information, fill in your company's e-mail address by themselves. Of course, you can fill the full operation and maintenance of coremail DMARC mailbox, you can directly copy the above DMARC records, coremail operation and maintenance engineers will timely analysis reports, and forge e-mail feedback to your company.
About DMARC record
- What is DMARC agreement?
- DMARC agreement works
- Other supporting information http://www.dmarc.org/
DMARC, the full name is Domain-based Message Authentication, Reporting and Conformance, it is based on the existing DKIM and SPF two leading email security protocols evolved.
The main purpose is to identify and intercept phishing e-mail, so that phishing is no longer enter the user's mailbox (inbox or trash), reducing the likelihood of a user opens the mailbox / read the phishing e-mail in order to protect the user's account password and other personal information security.
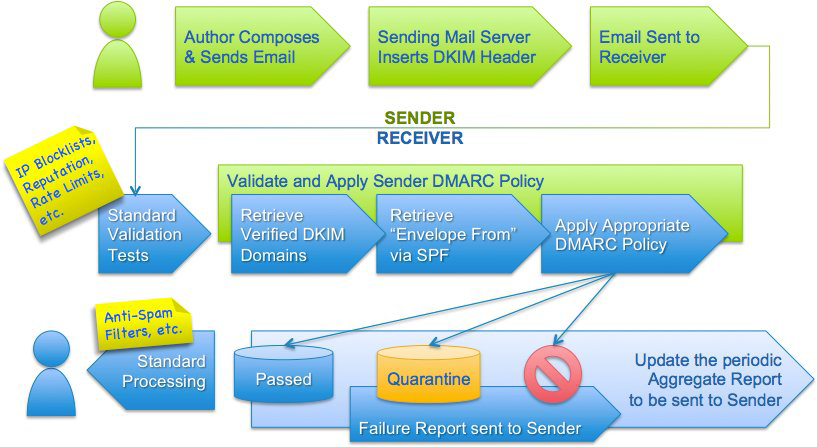
A DMARC policy allows a sender to indicate that their emails are protected by SPF and/or DKIM, and tells a receiver what to do if neither of those authentication methods passes – such as junk or reject the message. DMARC removes guesswork from the receiver’s handling of these failed messages, limiting or eliminating the user’s exposure to potentially fraudulent & harmful messages. DMARC also provides a way for the email receiver to report back to the sender about messages that pass and/or fail DMARC evaluation. The workflow is shown below: