Managing Anti-Spam
- • How to create a new sender rule?
- • How to add blacklist and whitelist?
- • How to create a new keyword rule?
- • About the parameter of "Global Settings"
- • What is tracking mail log?
- • You notice sent record of ip127.0.0.1 in email log, but the record shows no senders and recipients. The record shows that the connection is interrupted. Is that normal?
- • The sent records show that the mail triggered greylist and delivery again, what is the problem with it and how to resolve it?
- • What does "recipient's number restriction (from external sites)" mean in basic settings of Managing Anti-Spam?
- • What if I set the filter of emails sent by internal site as "Yes", what has it effect on?
- • What is greylist? What will happen if trigger greylist?
- • What does "Spam Fingerprint Filter Employment" of Advanced Settings mean?
- • What is spf? What if I do not select spf checking?
- • What if select RBL non-checking?
- • What does Fingerprint counter threshold filter?
- • Why should we update the Feature Database?
How to create a new sender rule?
To create a new filter rule, you can click "Create new sender rule" on the page of sender rules list. Set IP and email address to match filter condition and select operations you need according to navigation.And you also can click "Usage Specification" for further understanding when you are unfamiliar with the operation:
Set IP and email address to match filter condition if necessary.If enter more one conditions at the same time,these condition need to match corresponding rules at the same time and then these actions can be triggered.Four kinds of situation about condition settings:
- Mails from certain IP addresses
Enter * in the field of sender address and fill IP address needed to filter in the field of IP.
- Mail from certain email addresses
Enter target mail address in the field of sender and receiver, like abc@abc.com. The content of IP field is needed to handle separately. We suggest you enter 0.0.0.0-255.255.255 in IP address for setting blacklist rules. It means it will trigger this rule for any IP connnection to filter connection requests; And when you set whitelist, keep IP field blank. It means the system trigger this rule when it is not necessary to connect to users. The system examine if it is one of users of whitelist in the process of receiving emails. You can refer to the above methods when you set other types of rules. In brief, enter 0.0.0.0-255.255.255 in IP address field, which means any IP connection trigger rules and examine the connection request. And it do not examine filter when user connect to system if the field is empty. The settings can be NOT operations in sender and receiver address simultaneously. That is !uid1@domain.com, uid2@domain.com, NOT operation to addresses. If the first character is "!", it means the other users from addresses except for the filling in addresses.(Like "!1@1.com, 2@2.com, 3@3.com" means all users match this rules except for 1@1.com, 2@2.com, 3@3.com)
- Mail addresses from certain domains
Mail address fill in domain "abc.com",which means all email addresses with this domain. And ".abc.com" means all users with abc.com and branch domain.
- Mails of certain address from certain IP
Enter target IP into IP Address and target mail address into Mail Address. The field of priortity is filled with number between 1 with 1000. The larger the number is, the higher priortity. The expired date is empty, which means the expired date is not set any rule.
How to add blacklist and whitelist?
On the page of creating sender rule, click executing operation and you can select blacklist and whitelist.How to create a new keyword rule?
Click "Create keyword rule" on the page to create new filter rules for content:
Set rule name and matching keyword. You can set filter keyword of header, subject, text, and attachment name in Keyword Filter Type. Then select the further operations.
Select "Use Regular Expression" on the right side to create keyword filter rule through regular expression. For example, ".*" stands for 0 or multiple characters. "\" stands for escape character, like enter ".*\.exe" into "Attachment name keyword",
and select "Regular Expression" to filter all mails with attachments named .exe. Please refer to
Take creating rule to filter mails contain keyword "fapiaodaikai" for example to describe the process of creating a keyword rule.
- Select "Reject Deliver" operation;
- Enter "faipiaodaikai" into "Matching keyword" or select regular expression to fill "fa.{0,100}piao.{0,100}dai.{0,100}kai", and other options are default;
- Name the keyword rule, like "faipiaodaika" and make sure then create.
About the parameter of "Global Settings"
- Basic Settings
- The limit of the number of recipients (from external site)
-
Rule note: If administrator set it as "15", which means user a can receive mails from user b of outside station and these mails are only sent to 15 recipients.
If it triggers rules: rcpt to command return "450 Requested mail action not taken: too much recipient."
- The upper limit of size of mails for senders from external site
-
Rule note: It means the upper limit of size of mails for external users can not exceed 51200KB.
If it triggers rules: do not deliver mails
- When the content of Mail From command is empty
-
Rule note: When it is found that the content of Mail From command in mails from external user is empty, the system will reject this mail to keep it from delivering to internal users.
If it triggers rules: when this option is Reject, mail from command returns invalid.
- Whether filter mails from internal site
-
Rule Note:
When local users send mails, if the scores of mails exceed threshold, whether should system deliver these mails?If it triggers rules: data command returns "550 Requested action not taken: mail %s is rejected", mails do not deliver.
-
- The limit of the number of failure
- The upper limit of the number of failure for every connection of SMTP authentication
-
Rule note: SMTP authentication,that is system require that user can login SMTP server only if they provide account and password. The purpose of SMTP authentication is in order to keep from intrusion of spams. The limit of the number of failure for every connection of SMTP authentication can prevent test password continuously.
If it triggers rules: mail from command returns "550 Requested mail action not taken: too much fail authentications", and disconnect
- The upper limit of the number of command for every connection receiving
-
Rule note: Restrict the number of every connection to keep clients from sending too many commands. If the number of user failure to SMTP authentication exceeds 30, system will break this connection.
If it triggers rules: mail from or rcpt to command return "450 Requested mail action not taken: too much command", and disconnect
- The upper limit of wrong command for every connection acceptting
-
Rule note: As SMTP communication protocol communicates through the unit of command and commands from the software to send spams are always wrong, it causes system server consumes resource to handle these commands. Through this configuration, the system will be controlled to handle these resource used by spam emails. (If the limit of the number of failure commands in every connection, the system will break the connnection.)
If it triggers rules: If the limit of failure command exceeds, the system will auto break the connection.
-
- Control the frequency of IP connection
- The upper limit for IP co-connection
-
Rule note: Limit the number of IPs connecting with server at the same time to prevent IP in internal site from sending spams and IP outside from Dos attack.
If it triggers rules: when the certain IP connects, return "554 IP<%s> is rejected" and disconnect at once when it exceeds this limit.
- The upper limit of IP connection every 15 minutes/everyday
-
Rule note: limit the largest number of IP connection in latest 15 minutes/and this day
If it triggers rules: when the certain IP connect, return "554 IP<%s> is rejected" and disconnect at once when it exceeds this limit.
- The upper limit of IP SMTP authentication failure every hour
-
Rule note: limit the number of IP SMTP authentication failure to prevent to test password.
If it triggers rules: when the certain IP connects "554, it will return IP<%s> is rejected, smtp auth error limit exceed" and disconnect at once, if the number exceeds this limit.
- The number of Mail command IP users in every hour does not limit.(Unit %)
-
Rule note: Prevent to list all users through Mail FROM.
If it triggers rules: when the certain IP connects, return "554 IP<%s> is rejected, mail command error limit exceed\r\n" and disconnect at once when it exceeds this limit.
- The number of RCPT command IP users in every hour does not limit.(Unit %)
-
Rule note: Prevent to list all users through RCPT TO.
If it triggers rules: when the certain IP connects, return "554 IP<%s> is rejected, rcpt command error limit exceed\r\n" and disconnect at once when it exceeds this limit.
-
- Control the frequency of use sending emails
- The upper limit of number of user sending mails every 15 minutes/this day
-
Rule note: Record the number of mails that are from the certain user every 15 minutes/this day.
If it triggers rules: The system will record the number of mails users send, if administrator set upper limit as 20 and 200 and the number of user sending mails exceed the two limits, the remaining mails (or prompt tip: can not send mails) can not be sent to recipients.
- The upper limit of the number of recipients of mails from one user every 15 minutes/ this day
-
Rule note: Record the number of recipients of mails from one user every 15 minutes/this day, it is set as "-1" generally which means this option does not set upper limit.
-
- Filter score threshold settings
- Grey list filter score(Default is 7 and use list technology to block mails)
-
Rule note: Employ grey list and mail score technology to filter, the higher the score of mail is, the much the likelihood of spam is.
If it triggers rules: When the score of mail is more than this value and approval for grey list check, the mail are not delivered.
- Mark score(The default is 10 and add mark prefix into mail subject.)
-
Rule note: The higher the score of mail subject is,the much likelihood of spam is.
If it triggers rules: When the score of mail is more than this value, system will deliver this mail but mark [spam] before the mail subject.
- Segregating score (The default is 12 and save mail to users' spam folder.)
-
Rule note: The higher the score of mail content is,the more the likelihood of spam is.
If it triggers rules: If the score of mail is more than this value, the mail will delivery to user's spam folder.
- Block score (The default is 23, reject mails directly)
-
Rule note: The higher the score of mail is, the more the likelihood of spam is.
If it triggers rules: If the score of mails is more than this value, reject this mail.
-
- Advanced Settings
- If the ratio of IP failure exceeds limit, IP connection is pended for a while to not respond this IP.
-
Rule note: When the number of IP failure, this IP is pended for a while and can not connect.
- Use keyword filter/Use Spam Fingerprint Filter
-
Rule note: Check whether mail content contain keyword/calculate fingerprint for mail and judge whether it matches with the one of spam.
- Not check SPF
-
Rule note: Check whether the connected ip is the same as spf record of sender's domain.
- Not check RBL
-
Rule note: Not check realtime blacklist
- Fingerprint counter filter threshold (The default is 10,-1 means system does not use this feature)
-
Rule note: Limit the number of appearance of the same fingerprint.
If it triggers rules: do not deliver mails.
- Whether system allow authentication user is not equal to sender
-
If it triggers rules: mail from command return "553 Mail from must equal authorized user."
- authorize SMTP command whether mail user is equal to From user in mail header
-
If it triggers rules: data command return "550 Requested mail action not taken: Fake sender", do not deliver mails
What is tracking mail log?
The system remain all mails handling information,mail information including normal communication, filter and the situations of filter.These information can be checked in mail log. And mail log record mail subject,sender,receiver,IP,log time and result and etc.
Click "Mail Log Track",and the default is intraday log information.The "Result" in mail log display the situation of deliver of the mail and situation of the triggering rules.
| Cause | Explain |
|---|---|
| Normal | The mail do not trigger any spam filter rule and is already delivered normally; |
| Whitelist | The sender of mail is in the white list and not limited by spam filter; |
| Blacklist | This sender of mail is in the black list and it will be blocked; |
| Keyword limit | The mail triggers the certain option of matching keyword rule and is judged spam and blocked; |
| System limit | The mail triggers the default spam filter rules and is blocked; |
| Frequency limit | The number of connections from the source ip of the mail exceeds the limit and is the mail is blocked; |
| Virus mail | The mail is judged virus mail by current search virus engine and it is blocked; |
| pending IP | The source IP of this mail have triggered intelligent system filter some times and the IP is pended(can not pass in two minutes), and the mail from the IP is blocked. |
| SPF check do not pass | The mail trigger SPF check and and it is blocked. |
| The score of mail exceeds threshold. | The score of mail is reach the certain score and it is blocked; |
| Spam mail feature database filter | The mail triggers finger print feature filter of and it is blocked; |
| The number of similar mails exceeds threshold. | The mail returns the similarity and reachs the certain number,and it is blocked. |
| The IP of sending in RBL | The mail triggers the RBL filter and it is blocked. |
| IP reputation filter | Add IP reputation filter explain |
| mails in sideline | The mails are moved to sideline folder |
The system sort mails by log time in descending order. The administrator can search certain information of mail through subject, IP, sender and receiver.
You notice sent record of ip127.0.0.1 in email log, but the record shows no senders and recipients. The record shows that the connection is interrupted. Is that normal?
Normal.There is a program called sysmonitor(Coremail contains),and its function is to check the system normality regularly.The sent records show that the mail triggered greylist and delivery again, what is the problem with it and how to resolve it?
When a mail send to the mailbox that never send mails, the system executes greylist filter. If it hits greylist, system will require sender send mails after some time. If you send the same mail, it will reject delivery and you can wait for the system to solve or set the right whitelist.What does "recipient's number restriction(from external site)" mean in basic settings of Managing Anti-Spam?
It means the limit of number of recipient of external site when delivery.What if I set the filter of emails sent by internal site as "Yes", what has it effect on?
When the score of mail from users of internal site exceeds threshold to determine to delivery, it will return "550 Requested action not taken: mails is rejected" and the mail is not sent.What is greylist? What will happen if trigger greylist?
The greylist means the system suspects the mail is not the one from normal system; it will trigger greylist and reject temporarily to require mail server to deliver again.What does "Spam Fingerprint Filter Employment" of Advanced Settings mean?
Extract the mail finger print and match with the ones in spam feature database of system and reject the matching mails.What is spf? What if I do not select spf checking?
SPF is sender IP verification mechanism, and keep senders from forging the domain to send mails. For example, 163.com builds SPF record and declares its mail server IP address. The recipients will receive mails claiming they are from 163.com and search SPF records to judge whether the IPs of senders are the one as the declaring.SPF play an important role in avoiding forging domain to send spam and is default open.What if select RBL non-checking?
RBL is a real-time blacklist and it collects IP of server sending spams and it will update dynamically and it is default open.What does Fingerprint counter threshold filter?
FingerPrint extracts the mail feature to judge the similarity between two mails. When the number of mails judged similar mails reach or exceed the threshold, the system will believe the similar mails are spams and reject the mails.Why should we need to update the Feature Database?
Updating the Feature Database is the feature to ensure Anti-spam GT to anti-spam at realtime. It can update and filter feature database from remote feature data center to ensure system to have newest filter rules and newly found spams.
Under default status,the system sets connecting the remote feature data center and update the data regularly:
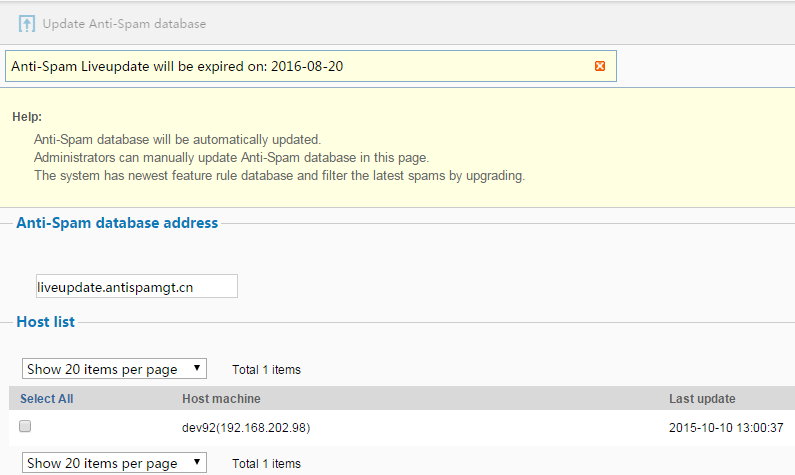
The page displays the expire date of updating feature database is 2016-08-20 and it means the system has the feature of updating automatically.
